FEDER:Access Control Model in IoT: Difference between revisions
Jump to navigation
Jump to search
No edit summary |
No edit summary |
||
| (2 intermediate revisions by the same user not shown) | |||
| Line 2: | Line 2: | ||
The main goal of this work is to define the access control model that can be used to express the access control policies for different access scenarios in IoTs system taking into account the privacy protection aspect since different types of sensors/devices are used in IoTs context (e.g. temperature sensor, movement sensor, CCTV, etc.) and some of which need privacy protection. | The main goal of this work is to define the access control model that can be used to express the access control policies for different access scenarios in IoTs system taking into account the privacy protection aspect since different types of sensors/devices are used in IoTs context (e.g. temperature sensor, movement sensor, CCTV, etc.) and some of which need privacy protection. | ||
==[[Access Control Requirements]]== | ==[[Access Control Requirements]]== | ||
In order to define the access control requirements, we need | |||
to consider different factors, such as legal issues, usage scenarios, | |||
deployment and usability. These factors are the primary | |||
keys to define the access control requirements based | |||
upon which the access control model is built. The detailed requirements can be found here: [[https://doc.info.fundp.ac.be/mediawiki/index.php/File:Feder_access_control_requirements.pdf]] | |||
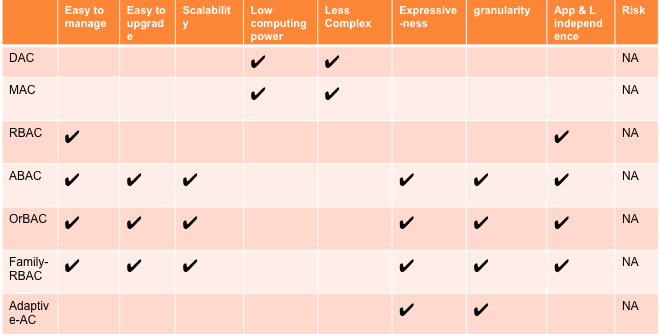
==[[Existing Models and comparison against defined requirements]]== | ==[[Existing Models and comparison against defined requirements]]== | ||
[[File:Slide10.png]] | |||
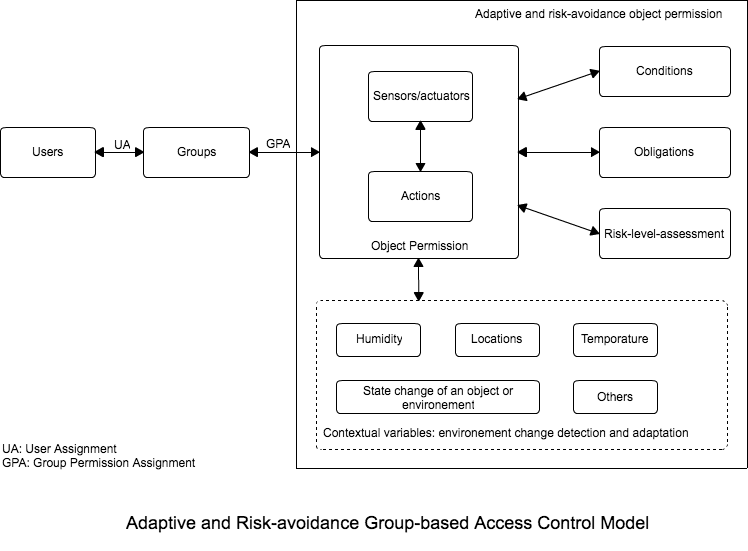
==[[Proposed Access Control Model]]== | ==[[Proposed Access Control Model]]== | ||
== AC Model == | |||
[[File:AC_model.png]] | |||
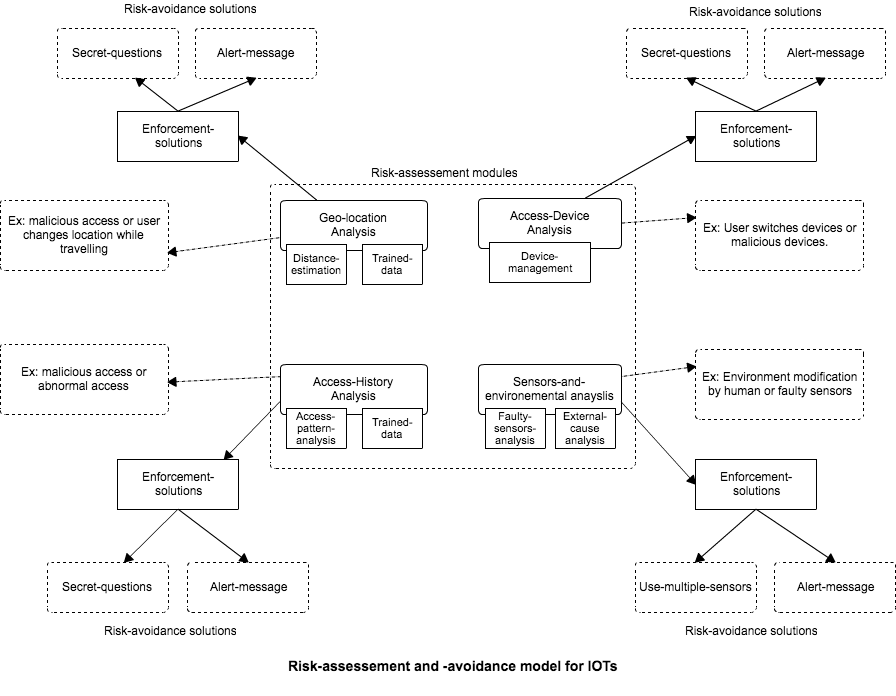
== Risk Assessment Model == | |||
[[File:Risk-assessement-model.png]] | |||
==[[Access Control Expression Language]]== | ==[[Access Control Expression Language]]== | ||
Latest revision as of 15:19, 5 March 2017
Objective
The main goal of this work is to define the access control model that can be used to express the access control policies for different access scenarios in IoTs system taking into account the privacy protection aspect since different types of sensors/devices are used in IoTs context (e.g. temperature sensor, movement sensor, CCTV, etc.) and some of which need privacy protection.
Access Control Requirements
In order to define the access control requirements, we need to consider different factors, such as legal issues, usage scenarios, deployment and usability. These factors are the primary keys to define the access control requirements based upon which the access control model is built. The detailed requirements can be found here: [[1]]
Existing Models and comparison against defined requirements
Proposed Access Control Model
AC Model