IDEE-FEDER project planning: Difference between revisions
Jump to navigation
Jump to search
No edit summary |
No edit summary |
||
| (24 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
= Project Planning= | |||
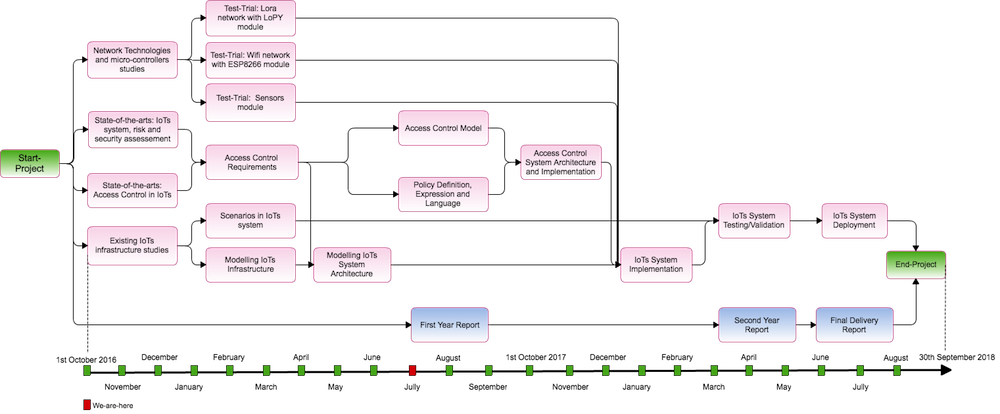
The project is for 2 years periods started from first of October 2016 to 30th September 2018. The entire project is broken down into small tasks as shown in the figure below. | |||
[[File:Planning IDEE.png]] | |||
*'''From October 2016 to January 2017:''' This phase focuses on building up the knowledge in the field of IoTs and most importantly the security issues in such system. We studies different areas under the IoTs context. | |||
**Existing IoTs infrastructure studies: The idea is to look at different existing IoTs system across domain from infrastructure/building to smart home and healthcare system. Different sources of information are considered both in research communities and private sectors. | |||
**State of the arts of IoTs: risks and security assessment: IoTs system allows different devices (things) to be connected through different communication medias (e.g.Internet, wifi, etc.). This opens an opportunity of larger attack. Thus, Identifying the risk and finding the solution to address such risk is important. | |||
* | ** State of the arts of access control in IoTs: In any data processing system, ensuring the access is granted to the right person is important in order to provide the trusting environment for people involved. Study the existing access control model for IoTs system is important in order to identify the strength and weakness of the model based on which we can make the conclusion whether existing model is sufficient or some extension is required. | ||
*Defining the access scenarios in | ** Network Technologies and micro-controller studies: Things in IoTs are devices controlled by the micro-controller, which are able to connect to network (Internet) and operate according to the user's command or in the automatic way. There are number of brands producing different type of micro-controllers that can be used in IoTs context. Study their specifications provide us some insides based on which we can choose the devices fitting to our requirements. We investigated two network technologies: WiFi and Lora network. For micro-controllers, we studied ESP8266 and LoPy of Pycom. | ||
* | *'''From January 2017 to April 2017:''' This phase focuses on some testing and trial and also some studies of the existing IoTs infrastructure. | ||
* | **'''Test-trial: Lora Network with LoPy:''' Our aim is to investigate the Lora network technology with different configurations and devices' specifications. We have tested Lora network with different gateways and devices such as iC880-A USB gateway with LoPy devices and we also tested LoPy as nano-gateway. We also tested for different frequencies and bandwidths. The tests are performed for both up and down link with ABP and OTAA modes. | ||
* | **'''Test-trial: Wifi network with ESP8266 module:''' We created the wifi network with ESP8366 and tested some smart-home scenarios with different type of sensors such as, temperature, luminosity, pressure, movement sensors. | ||
* | **'''Test-trial: Sensors module:''' Different types of sensors are tested with ESP8266 and LoPy micro-controller. Sensors used in our tests are temperature, pressure, humidity, luminosity and movement sensors. | ||
* | **'''Scenarios in IoTs system:''' Defining the access scenarios in IoTs system, more importantly in smart-home and healthcare domains. The scenarios are derived from our studies of needs in smart home system and healthcare information system. The list of scenarios can be found at https://doc.info.fundp.ac.be/mediawiki/index.php/File:List_of_Smart_Home_Scenarios.pdf | ||
* | **'''Access Control Requirements:''' To define the access control requirement, we need to study both the scenarios, security requirements for processing data in IoTs context and also the legal requirements. European Laws are our sources of information used to derived the access control requirements. The detailed access control requirements can be found at https://doc.info.fundp.ac.be/mediawiki/index.php/FEDER:Access_Control_Requirements_in_IoT | ||
**'''Modelling IoTs infrastructure''': This task focuses on defining the IoT meta model that can be used to model different IoTs infrastructure such as smart-home, healthcare, smart-monitoring or transport monitoring system. The meta-model takes into account both the functionality and security issues. | |||
*'''From April 2017 to July 2017''': This phase focuses on modelling a formal IoTs system architecture that will be used for the implementation and testing in future phase. Two domains are considered, smart-home and healthcare system. | |||
*'''From July 2017 to September 2017''': This phase focuses on the definition of access control model, policies definition and expression and the study of access control policy language that will be used in the system implementation in future phase. The first progress report is also done in this phase. | |||
**Access Control Model: Based on our study on existing access control models in IoTs in the first phase of the project and the study of the access control and legal requirements, we define access control model, which can be used to express access control policies in our defined scenarios and security requirements. The model should comply with the requirements we defined in https://doc.info.fundp.ac.be/mediawiki/index.php/FEDER:Access_Control_Requirements_in_IoT | |||
**Policy Definition, Expression and Language: This task focuses on defining the access control policy language to be used to express the access control policies derived from the model done in the early task. We will take a look at different existing access control policy languages such as, XACMl, EPAL and ODRL. The selection of the language will be based on how it fits into the requirements of the defined access control model. | |||
*'''From September 2017 to December 2017''': This phase focuses on defining the access control system architecture and its implementation. The future access control engine should be able to validate the access control policies expressed based on the access control model done in the early phase of the project. | |||
*'''From December 2017 to March 2018''': IoTs system implementation: Based on the IoTs system architecture done in the early phase of the project and the access control system. We integrate both modules together to make one functional system that is able to provide the security required to process the data generated from different sensors and to be able to serve all user's requests with different usage scenarios in IoTs environment. | |||
*'''From March 2018 to to June 2018''': Once IoTs system is built, testing and validation of such system against the defined scenarios and requirements are important. The testing and validation criteria are performance, security and usability. Second progress report is also built in this phase. | |||
*'''From June 2018 to 30th September 2018''' IoTs system deployment: an official deployment and testing is done in this final state of the project. Final demonstration to concerned partners may also be done in this phase of the project. The final deliverable report of task T1.3.4 is also done in this phase. | |||
Latest revision as of 15:19, 12 February 2018
Project Planning
The project is for 2 years periods started from first of October 2016 to 30th September 2018. The entire project is broken down into small tasks as shown in the figure below.
- From October 2016 to January 2017: This phase focuses on building up the knowledge in the field of IoTs and most importantly the security issues in such system. We studies different areas under the IoTs context.
- Existing IoTs infrastructure studies: The idea is to look at different existing IoTs system across domain from infrastructure/building to smart home and healthcare system. Different sources of information are considered both in research communities and private sectors.
- State of the arts of IoTs: risks and security assessment: IoTs system allows different devices (things) to be connected through different communication medias (e.g.Internet, wifi, etc.). This opens an opportunity of larger attack. Thus, Identifying the risk and finding the solution to address such risk is important.
- State of the arts of access control in IoTs: In any data processing system, ensuring the access is granted to the right person is important in order to provide the trusting environment for people involved. Study the existing access control model for IoTs system is important in order to identify the strength and weakness of the model based on which we can make the conclusion whether existing model is sufficient or some extension is required.
- Network Technologies and micro-controller studies: Things in IoTs are devices controlled by the micro-controller, which are able to connect to network (Internet) and operate according to the user's command or in the automatic way. There are number of brands producing different type of micro-controllers that can be used in IoTs context. Study their specifications provide us some insides based on which we can choose the devices fitting to our requirements. We investigated two network technologies: WiFi and Lora network. For micro-controllers, we studied ESP8266 and LoPy of Pycom.
- From January 2017 to April 2017: This phase focuses on some testing and trial and also some studies of the existing IoTs infrastructure.
- Test-trial: Lora Network with LoPy: Our aim is to investigate the Lora network technology with different configurations and devices' specifications. We have tested Lora network with different gateways and devices such as iC880-A USB gateway with LoPy devices and we also tested LoPy as nano-gateway. We also tested for different frequencies and bandwidths. The tests are performed for both up and down link with ABP and OTAA modes.
- Test-trial: Wifi network with ESP8266 module: We created the wifi network with ESP8366 and tested some smart-home scenarios with different type of sensors such as, temperature, luminosity, pressure, movement sensors.
- Test-trial: Sensors module: Different types of sensors are tested with ESP8266 and LoPy micro-controller. Sensors used in our tests are temperature, pressure, humidity, luminosity and movement sensors.
- Scenarios in IoTs system: Defining the access scenarios in IoTs system, more importantly in smart-home and healthcare domains. The scenarios are derived from our studies of needs in smart home system and healthcare information system. The list of scenarios can be found at https://doc.info.fundp.ac.be/mediawiki/index.php/File:List_of_Smart_Home_Scenarios.pdf
- Access Control Requirements: To define the access control requirement, we need to study both the scenarios, security requirements for processing data in IoTs context and also the legal requirements. European Laws are our sources of information used to derived the access control requirements. The detailed access control requirements can be found at https://doc.info.fundp.ac.be/mediawiki/index.php/FEDER:Access_Control_Requirements_in_IoT
- Modelling IoTs infrastructure: This task focuses on defining the IoT meta model that can be used to model different IoTs infrastructure such as smart-home, healthcare, smart-monitoring or transport monitoring system. The meta-model takes into account both the functionality and security issues.
- From April 2017 to July 2017: This phase focuses on modelling a formal IoTs system architecture that will be used for the implementation and testing in future phase. Two domains are considered, smart-home and healthcare system.
- From July 2017 to September 2017: This phase focuses on the definition of access control model, policies definition and expression and the study of access control policy language that will be used in the system implementation in future phase. The first progress report is also done in this phase.
- Access Control Model: Based on our study on existing access control models in IoTs in the first phase of the project and the study of the access control and legal requirements, we define access control model, which can be used to express access control policies in our defined scenarios and security requirements. The model should comply with the requirements we defined in https://doc.info.fundp.ac.be/mediawiki/index.php/FEDER:Access_Control_Requirements_in_IoT
- Policy Definition, Expression and Language: This task focuses on defining the access control policy language to be used to express the access control policies derived from the model done in the early task. We will take a look at different existing access control policy languages such as, XACMl, EPAL and ODRL. The selection of the language will be based on how it fits into the requirements of the defined access control model.
- From September 2017 to December 2017: This phase focuses on defining the access control system architecture and its implementation. The future access control engine should be able to validate the access control policies expressed based on the access control model done in the early phase of the project.
- From December 2017 to March 2018: IoTs system implementation: Based on the IoTs system architecture done in the early phase of the project and the access control system. We integrate both modules together to make one functional system that is able to provide the security required to process the data generated from different sensors and to be able to serve all user's requests with different usage scenarios in IoTs environment.
- From March 2018 to to June 2018: Once IoTs system is built, testing and validation of such system against the defined scenarios and requirements are important. The testing and validation criteria are performance, security and usability. Second progress report is also built in this phase.
- From June 2018 to 30th September 2018 IoTs system deployment: an official deployment and testing is done in this final state of the project. Final demonstration to concerned partners may also be done in this phase of the project. The final deliverable report of task T1.3.4 is also done in this phase.